Inside the $4.5 Billion Bitcoin-Laundering Saga: Exclusive Q&A Session With Chainalysis Co-Founder

In a historic turn of events marking the pinnacle of cryptocurrency-related crime investigations, the U.S. Department of Justice triumphed in what they termed the “largest financial seizure” involving a staggering $4.5 billion Bitcoin-laundering scheme.
At the heart of this saga were Ilya Lichtenstein and Heather Morgan, the latter also known by her rap alias Razzlekhan. The duo, arrested in connection with the 2016 Bitfinex hack, recently pleaded guilty, shedding light on a case that showcases the intersection of cutting-edge blockchain analysis and traditional investigative prowess.
Background Story
The heist unfolded on August 2, 2016, when Bitfinex, a global cryptocurrency exchange giant, fell victim to a breach. In a swift move lasting less than two hours, approximately 120,000 Bitcoins vanished, scattered across 2,075 addresses under the hacker’s control. This cataclysmic event set the stage for a high-stakes pursuit that would eventually lead to the doorsteps of Lichtenstein and Morgan.
Law enforcement agencies orchestrated a collaborative effort involving Chainalysis, the Internal Revenue Service Criminal Investigation (IRS-CI), the Department of Justice (DOJ), and the Federal Bureau of Investigation (FBI). This coalition exemplified the synergy between blockchain analytics and traditional financial investigation techniques, resulting in the recovery of an astounding 94,643 Bitcoins, equivalent to roughly $3.6 billion.
The brilliance of blockchain, hailed for its immutable ledger, played a pivotal role in tracking the pilfered funds from Bitfinex to the hackers’ wallets and, eventually, to a stash under the control of the U.S. government. This transparent trail, a testament to the blockchain’s permanence, unequivocally demonstrated the transfer of funds from the victimized exchange to the possession of law enforcement, marking the largest asset recovery from a theft in history.
The recent filings in the case unveiled the guilty plea of Lichtenstein and Morgan, who were not only implicated in laundering the stolen Bitcoin but also revealed Lichtenstein’s role as the orchestrator behind the hack itself—a startling revelation that added layers of complexity to the unfolding narrative.
The seized assets continued to mount, with subsequent recoveries occurring on August 9th, 2022 (12,267 Bitcoin), November 18th, 2022 (1,155 Bitcoin), and January 5th (2.5 Bitcoin), culminating in a total haul of over 108,068 Bitcoin by U.S. authorities.
Examining the evolution of the husband-and-wife duo’s money laundering tactics following the Bitfinex hack reveals a sophisticated strategy that kept authorities engaged in a relentless pursuit.
Tracking of Funds
The tracking of Bitfinex’s pilfered funds, detailed in a Chainalysis Reactor graph based on a public DOJ indictment, reveals a multifaceted money laundering trajectory orchestrated by Lichtenstein and Morgan.
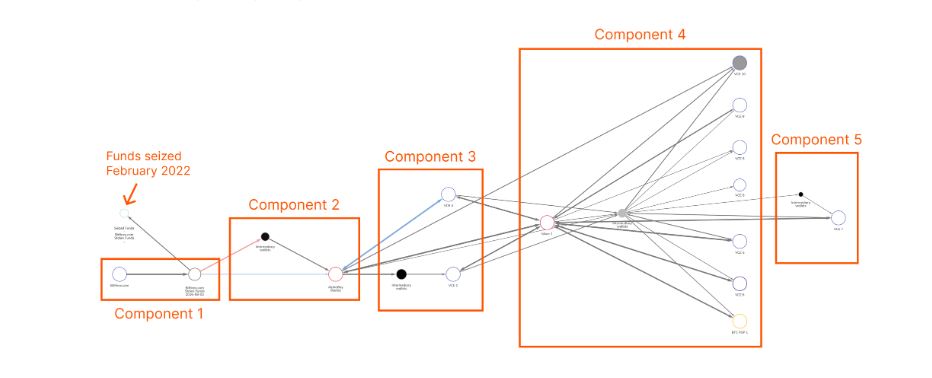
The laundering process encompasses five key components spanning diverse cryptocurrency entities and timeframes:
- The Theft: 120,000 Bitcoin from Bitfinex moved to a labeled “Bitfinex.com Stolen Funds” wallet. Law enforcement seized most of these funds in February 2022, relocating them to a new wallet.
- Darknet Market Usage: Funds transferred to the defunct AlphaBay market in January 2017, acting as a mixer for depositing and withdrawing equivalent Bitcoin amounts.
- Transfers to VCEs and Initial Cashouts: Funds moved from AlphaBay to four virtual currency exchanges (VCEs 1-4). Lichtenstein and Morgan used fake identities to receive laundered Bitcoin, but suspicious activity led some exchanges to freeze accounts.
- Mixer Employment and Further VCE Transactions: Post-AlphaBay takedown in 2019, funds were routed through a popular mixer, then traded at additional VCEs (VCEs 5-10). They diversified assets, including Monero, and attempted to exchange cryptocurrency for gold through a merchant services provider.
- Conversion to Fiat and Gift Card Transactions: In 2020-2021, conversion of more funds into fiat currency at VCE 7 occurred, deposited into a U.S. bank account. Additionally, gift cards for retailers like Walmart were purchased through specialized service at VCE 10, dedicated to crypto-for-gift card trades.
While the DOJ indictment anonymizes entities and references them as Virtual Currency Exchanges (VCEs), showcasing a distinct evolution in the couple’s laundering strategy, some exchanges detected suspicious activity or froze accounts due to unverified identities or unclear fund origins.
The intricate maneuvers by Lichtenstein and Morgan spanned multiple platforms and tactics, from utilizing darknet markets as mixers to diversifying assets and attempting to pass off Bitcoin as payment for advertising services. This web of transactions ultimately led to cash exchanges and the procurement of gift cards in a prolonged, multifaceted money laundering journey.
Q&A Session with Chainalysis
UNLOCK Blockchain reached out to Jonathan Levin, Co-Founder and Chief Strategy Officer at Chainalysis, seeking insight into the incident; specifically, to understand the pivotal role that blockchain analysis played in unraveling the intricate money laundering strategy.

Presenting the Dialogue: Questions and Their Corresponding Responses
- Could you explain how blockchain analysis played a crucial role in unravelling the money laundering strategy of Ilya Lichtenstein and Heather Morgan? What were the key insights that blockchain analysis provided?
The inherent transparency of blockchains meant that despite the efforts taken by the perpetrators of the attack to hide any activity, law enforcement was able to track the flow of funds across the 5 ‘components’ of the couple’s money laundering strategy, as explained in the ‘Tracking of Funds’ section.
While this is an extremely high-level and simplified overview of how authorities identified the perpetrators behind the hack, it highlights the extent to which cryptocurrencies can be tracked despite the many steps hackers might take to try to launder their stolen funds. The analysis provides insight into the techniques that hackers attempt to use — ranging from utilizing darknet markets to launder funds, exchanges to try to convert these into fiat currencies, to even specialized services to purchase gift cards. This case illustrates how blockchain analysis combined with traditional investigation techniques can empower law enforcement to investigate cryptocurrency-related crime, win convictions, and seize stolen funds — in this case, the equivalent of billions worth of crypto at the time of arrest.
- The investigation spanned several years and involved multiple stages of the money laundering process. Could you discuss any challenges that arose in maintaining a coherent view of the evolving strategy over time?
By design, transactions entered into the blockchain remain indelible and immutable through the entire life of the ledger. This means that despite the passage of time, these transparent records are unmoved and unaltered.
Complexity can arise from the various obfuscation techniques that hackers use in their attempts to cover their tracks. However, because of the permanence of blockchain records, authorities can revisit old cases and potentially solve past crimes, as Chainalysis becomes more sophisticated.
- The Bitfinex case serves as a remarkable example of cooperation between law enforcement and cryptocurrency-focused companies like Chainalysis. Could you share your thoughts on how such collaborations could shape the future of tackling cryptocurrency-related crimes?
As cryptocurrency adoption grows, it will increasingly be used by both good and bad actors. Government agencies need the training and tools to investigate illicit crypto activity ranging from scams and hacks to terrorism financing and beyond. Law enforcement will also need resources to confidently identify and seize crypto assets.
- In cases like these, where the stolen funds have been seized and returned to their rightful owners, what impact does this have on the broader cryptocurrency ecosystem in terms of building trust and mitigating risks?
As hackers continue to target businesses and individuals, this case demonstrates how the transparency and permanence of the blockchain can assist in recovery. Working with the private sector, law enforcement can leverage technology and techniques to keep the industry safe. As governments continue to roll out regulations for exchanges and VASPs, many of the avenues hackers have leveraged to launder their funds have become impractical or outright infeasible. It sends a strong message of deterrence to would-be crypto criminals and strengthens consumer confidence.
- Looking ahead, what are the key lessons learned from this case that can guide law enforcement agencies, cryptocurrency exchanges, and other stakeholders in preventing and addressing similar cases of cryptocurrency-based crimes?
There is no doubt that a growing utilization of cryptocurrencies has been taking place around the world. With these digital currencies becoming mainstream, the onus is on regulators, law enforcement agencies and judiciaries to educate themselves on the topic, and arm themselves with the tools they need to effectively carry out investigations. We are already seeing this in forward-focused countries such as the UAE where the nation’s Ministry of Artificial Intelligence, Digital Economy and Remote Work Applications has signed a preliminary agreement with us to provide virtual training programmes for the country’s government entities.
In the long term, it’s important to raise awareness around the fact that the transparency of blockchains makes crypto a poor medium for money laundering. It also affords governments and financial institutions the opportunity to build safer, more transparent, and more inclusive financial systems. With the right data, training, and tools, the public and private sectors can work together to achieve this highly desirable objective.
The Bitfinex investigation stands as a testament to the strides made in the fight against crypto-related crime, emphasizing the imperative synergy between law enforcement agencies and the cryptocurrency industry.
As hackers continue to target entities and individuals, the Bitfinex case provides a blueprint highlighting how the indelible traces on the blockchain can be instrumental in recovering stolen assets, bolstering confidence in the safety and security of the digital economy.





